
Maksim Kabakou - Fotolia
Why this quantum computing breakthrough is a security risk
Quantum computing will void pretty much all security encryption techniques and open the door to hackers. Here's how to protect your data when it does.
It's coming. Just about all the encryption security we've come to rely upon to protect our assets will go out the window when the quantum computing breakthrough becomes commonplace in the developer community. It will be a hacker's paradise. Allow me to elaborate.
The fundamental theory behind data encryption is that we can hide data by applying an encryption algorithm and thus transform it into an indecipherable format. Someone can only then decipher the data by using a unique private key in the sole possession of approved personnel. Trying to unlock the data without the key can take decades of trial-and-error computation on a classical computer. The inherent deterrent is that nobody can or wants to spend years trying to crack the algorithm.
But what if the period of trial and error went from decades to minutes? In this case, the allure of cracking the code becomes compelling. Increased levels of malicious intention become inevitable.
The quantum computing breakthrough provides the processing power needed to reduce the amount of time it takes to hack encrypted data. And quantum computing is here now. The security risks are very real.
How quantum computing puts encryption at risk
Quantum computers work in a fundamentally different way than any computer that has come before. Mainstream computers, aka classical computers, use binary computation to get work done. The processors used in classical computers -- think: Intel, Advanced Micro Devices, Nvidia and Qualcomm processors -- do calculation by manipulating bits, which are binary digits, zeroes and ones. Quantum computers use a computational unit called a qubit -- a quantum bit. While a bit can only be in one state -- 0 or 1 -- at any single time, a qubit can be in two states simultaneously -- 0 and 1. The ramification of qubits and the quantum computing breakthrough is that the speed of calculation increases dramatically.
For example, finding the prime factors of this number: 7,894,230,148,392,014,768,329,075,957,274,239,743,189,247,328,944,398,
392,139,139,168,297,436,118,432 on a classical computer can take years. On a quantum computer, it takes minutes.
Quantum is well-suited for these sorts of tasks, like finding data hidden within a heavily encrypted byte array. Yes, the quantum computing breakthrough is almost magical in a way, but it is indeed very real. In fact, you can now go to the IBM Quantum Experience site and do calculations using a quantum computer for free. So, given the right set of circumstances, anybody with malicious intent can hack any password.
So, what's to be done?
Although the security threats the quantum computing breakthrough pose are real and probable, there are ways to avoid the hazards at hand. Some remedies can be implemented now; others will require some degree of technological innovation to become mainstream. But let's assess three viable options to meet the threats at hand.
Can't hack what you can't get to
The first thing you can do to quantum-proof your enterprise -- or at least make it somewhat resilient -- is make sure that as few people as possible can get to the encrypted data. This means following basic, modern security practices. Most notably, this means locking down firewalls, using multifactor authentication and never storing access data in the persistent storage of an application. That might seem obvious, but you'd be surprised how many enterprises are still pretty lax -- so much so that Amazon Web Services now offers a service, Macie, that uses machine learning to traverse your infrastructure to find and report just these types of security exposures.
Use quantum-resistant cryptography
Another way to avoid the impending security threats is to use quantum-resistant cryptography. Quantum-resistant cryptography goes beyond common RSA techniques and offers protection intended to withstand the perils of quantum-based hacking.
The most immediate step is to increase the size of the encryption key beyond current standards. For example, you could increase the key size to 256 bits. Also, you can use a symmetric key algorithm, where both parties in the message exchange share the same secret. A large bit key provides an added layer of security.
Increasing key size and using a symmetric key algorithm are but two of the approaches under consideration. Also, there is research exploring ideas like lattice-based cryptography, multivariate cryptography, hash-based cryptography and supersingular elliptic curve isogeny cryptography. One needs a firm understanding of complex mathematics and cryptography, well beyond the grasp of some high schooler lurking in a nefarious corner of the internet, to crack the code behind each of these new approaches. Rather, both defenders and perpetrators interested in quantum-resistant cryptography will typically be large-scale entities, most likely sovereign national governments or large corporations determined to protect or compromise a mission-critical asset.
Implement the use of quantum signatures
Quantum signatures combine the benefits of quantum-resistant encryption with asymmetric key exchange between the sender and receiver of a message. A quantum signature encrypts data with quantum keys that are fundamentally indeterminate. In other words, due to the multistate nature of quantum computing, the encryption key can never be fully known by hackers, even with their own quantum computer. As mentioned, the only way to decipher the message is for the sender and receiver to use the private key decryption. However, in this scenario, the private key never leaves the possession of the owner.
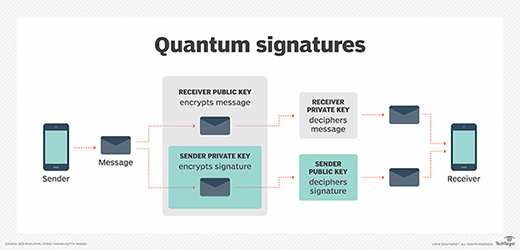
The way that the asymmetric key scenario works is that the sender encrypts the message according to the receiver's public key. Also, the sender sends a digital signature, encrypted with the sender's private key, which the receiver decrypts using the sender's public key. The digital signature contains the sender's message, too. If the two versions of the message the receiver gets -- the one sent to the receiver and the one encrypted in the message -- do not match, then the receiver knows there is a problem.
All parties' keys are generated using quantum computing. Both parties -- sender and receiver -- know about each other by way of data exchange between private and public keys.
(Yes, once again, it's somewhat magical. But as we learned with breaking the code generated by the Enigma machine, the only way to beat a machine is with another machine.)
Advancement comes with risk
The quantum computing breakthrough is going to have a positive impact on many areas of the digital landscape. Computationally intensive tasks, like weather prediction and generic research, will become a breeze as quantum computing becomes more mainstream. However, as with any great advancement, there are risks along the way. The security problems posed by quantum computing are significant, so much so that the National Institute of Standards and Technology has been actively engaged in ongoing research to address the problems at hand and is inviting other organizations to contribute to its work.
We have solutions at hand. History has shown that human imagination, when adequately informed, has the capacity to solve problems once thought unsolvable. We are forewarned; hence, we are forearmed. Now, the work is to solve the security problems that will appear on the horizon as the quantum computing breakthrough becomes part of the modern, technical landscape.









