
Getty Images
Know how and when to use blockchain vs. distributed ledgers
Blockchain and distributed ledgers are similar but not quite synonymous. Learn their differences and how they are used, including together, for transactions and data storage.
There is a perception among many that blockchain and distributed ledger technology are the same thing. This is not quite the case.
This article explains the difference between blockchain and distributed ledger technology (DLT) and how each is used. First, we'll cover the essentials of blockchain and how DLT uses blockchain rather than being a substitute for it. Then, we'll describe how DLT uses other types of peer-to-peer technologies to store data.
Understanding the blockchain foundation
Blockchain is a consensus driven, peer-to-peer (P2P) technology in which data is stored immutably, in an identical manner among a large number of computers. Every computer on the blockchain network, called a node, hosts identical copies of the blockchain.
User-submitted transactions are transformed into blocks and added to the blockchain that runs on a given node. Once a block is added to a node's blockchain, the block propagates to all the other nodes on the blockchain network. To add a block to a blockchain, the nodes on the chain must come to a consensus that the block is OK to add (see Figure 1 below).
That consensus can be achieved in various ways. The given blockchain supports a particular consensus algorithm; two common examples of consensus algorithms are proof of work and proof of stake.
Once a piece of data is stored on the blockchain, it can never be changed. Moreover, no single computer is the sole source of truth for the data on the blockchain. If one computer on a blockchain network goes down, other computers that store the same data provide service. A blockchain network can be public or private, although the usual scope for a blockchain is public.
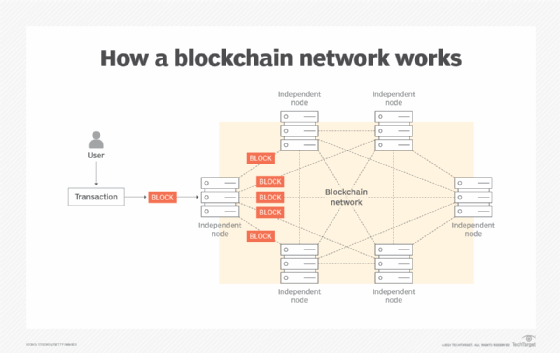
To conceptualize a blockchain, consider a spreadsheet that is distributed identically in a P2P manner. In this analogy, each row in the distributed spreadsheet is equivalent to a block on the blockchain. Once a row is added to the spreadsheet it can never be removed nor its data changed. The same is true of a block added to a blockchain.
In addition to storing data, some blockchains have the capability to store and execute smart contracts. In the next section we'll discuss how smart contracts add a great deal of power and flexibility to blockchain technology.
Using blockchain with a DLT
Distributed ledger technology takes a decentralized approach to data storage, with no controlling central database server or systems administrator.
As mentioned above, a distributed ledger can use the blockchain as a data storage mechanism. Some blockchains support hosting smart contracts, which are programmed logic stored according to a particular address on the blockchain and executed on the blockchain. Think of a smart contract as a stored procedure that runs on a centralized database. Ethereum and Solana are examples of blockchains that support smart contracts.
Most blockchains publish a component called a blockchain virtual machine to help developers interact with the given blockchain, particularly for interactions that involve smart contracts hosted on the given chain. Consider a blockchain's virtual machine as equivalent to the Java Virtual Machine (JVM), which is an intermediary layer between an application and a computer's underlying operating system. In the same way, a blockchain virtual machine is the intermediary between an application and the underlying blockchain (see Figure 2).
Some blockchains support a common virtual machine, such as the Ethereum Virtual Machine (EVM). The EVM is supported by the Ethereum and Hedera blockchain networks as well as the Polygon network and Binance Smart Chain, to name a few. Support for a common EVM not only makes it easier for a developer to write distributed applications for a given blockchain, it helps developers write distributed apps that interact with numerous blockchains.
For all the value that a blockchain provides to a DLT, there is a major problem of latency. Validating and adding a block to the given blockchain requires much time-consuming consensus and distribution activities. Some DLTs that use a blockchain attempt to address latency through what is called Layer 2 technology (L2) that increases the speed and cost of transaction processing. L2 operates off-chain in conjunction with the blockchain to assume some labor-intensive tasks, so the blockchain only does work that is essential and exclusive to the chain (see Figure 2).
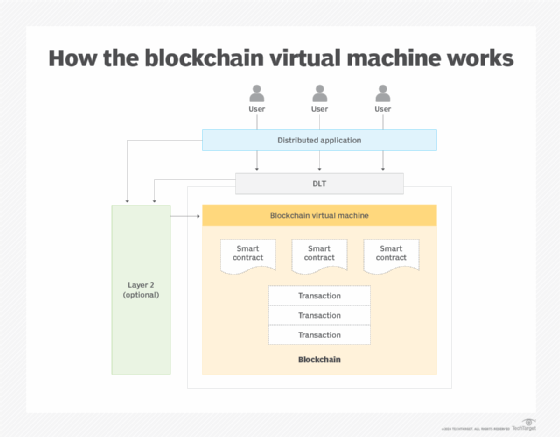
As mentioned earlier, blockchain has become the popular storage technology for distributed ledger technology. However, it's not the only way for a DLT to store data. Let's look at some alternatives.
Alternative storage technologies for DLT
By definition, distributed ledger technology has no central authority and no central point of failure. All components within a distributed ledger work on a P2P basis. Thus, any data storage technology used by a DLT must also support a P2P architecture (see Figure 3).
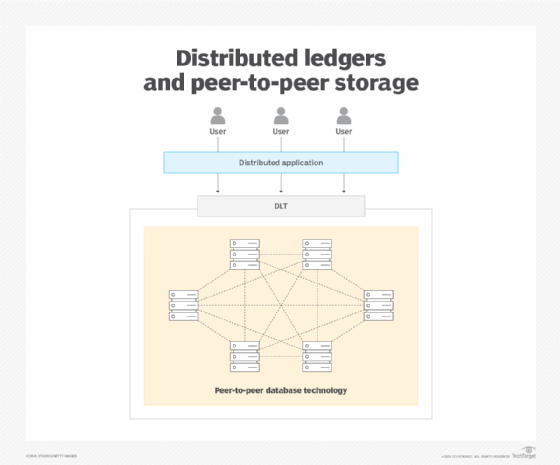
Blockchain happens to be the popular blockchain storage technology, but there are many alternatives. The following examples, listed in alphabetical order and based on my general research, describe a few of the many P2P databases that can be used with a DLT.
BitTorrent
Created in 2001, BitTorrent is the granddaddy of peer-to-peer databases. It started out as a way for users to share video and audio files, but today BitTorrent is used by both public and private organizations. For example, the U.K.'s Combined Online Information System shares information about the government's spending, and since 2010 Facebook uses BitTorrent to push updates to its server. While BitTorrent is not exclusively database technology, it can be the underlying storage mechanism for a DLT.
Gun
Gun's interesting feature is that the node hosting an instance of Gun determines the data to share with the other nodes on the network. Gun uses the Daisy-chain Ad-hoc Mesh-network (DAM) as its P2P networking algorithm. Gun is intended to run in a browser, on a Node.js server or on a mobile device using React Native.
OrbitDB
OrbitDB uses the InterPlanetary File System (IPFS) as its storage component and Libp2p Pubsub to synchronize data among peers operating on the network.
Tableland
Tableland, an open source, permissionless cloud-based database, is built on SQLite and publishes an SQL-like querying language to execute transactions and query the underlying data. A DLT can use Tableland as a standalone database or in conjunction with smart contracts stored on an EVM compatible blockchain. Users must have a cryptographic wallet such as MetaMask to access it through a browser.
Putting it all together
Blockchain and distributed ledgers have come a long way since their initial uses as the underlying storage technology for Bitcoin and distributed applications for online gaming, respectively.
Today, all the major cloud providers offer blockchain products: AWS' Managed Blockchain and Quantum Ledger Database, Google's Blockchain Node Engine and Microsoft Azure's Confidential Ledger, to name a few.
These technologies are here to stay. Moving forward, the trick is to use them appropriately and safely. At the least, this means one must understand the difference between blockchain and distributed ledger technologies and when to use them best.
Bob Reselman is a software developer, system architect and writer. His expertise ranges from software development technologies to techniques and culture.











