How to use GitHub Actions secrets to hide your tokens and passwords example
GitHub Actions Secrets example
One of the ongoing challenges DevOps professionals face when developing continuous integration workflows that integrate with disparate systems is how to protect that passwords, secret keys and tokens required to authenticate against them. That’s where the GitHub Actions secret comes in. It provides a secure vault to store your confidential information, and a simple mechanism to access those secret tokens in your GitHub Actions scripts.
Secret tokens and GitHub Actions
From the Settings tab of any repository, there’s an option to add a GitHub Actions secret. Simply provide a name for the secret and a corresponding value and click the green Add secret button. The convention for how to name a GitHub Actions secret is screaming snake case, but the convention is not enforced by any compilers.
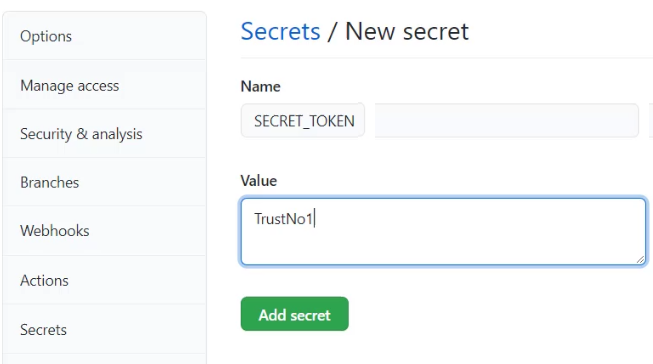
Screaming snake case is the convention to name GitHub Actions secrets.
Within your GitHub Actions CI/CD pipelines, simply prepend the word secret before the name you assigned your passphrase, and escape it as a YAML variable, and the GitHub Actions secret will be passed to your scripts.
| Git, GitHub & GitHub Copilot Certification Made Easy |
|---|
| Want to get certified on the most popular AI, ML & DevOps technologies of the day? These five resources will help you get GitHub certified in a hurry.
Get certified in the latest AI, ML and DevOps technologies. Advance your career today. |
Here’s how a reference to a GitHub Actions secret would present itself in a YAML build file:
${{ secrets.SECRET_TOKEN }}
GitHub Actions secret example
Here is an example of a GitHub Actions job that executes a conditional statement based on a secret GitHub Actions token:
# Use a GitHub Actions secret variable in a bash shell - name: Step 2 - GitHub Action if statement (true) env: WHO_TO_TRUST: ${{ secrets.SECRET_TOKEN }} if: env.WHO_TO_TRUST == 'TrustNo1' run: echo "I know what the secret token is!"
You can find the full YAML file for this example on GitHub.
How to log GitHub Actions secret
Given that fact that a developer could lose their job and possibly be sued for millions of dollars if they ever logged the actual text of a password, it’s good to know that any attempt to print out or log a password in a GitHub Action will fail, and only a masked set of asterixis will be output. For testing and evaluation purposes, you might want to see the GitHub Actions secret value. You can achieve this by manipulating the text and streaming the manipulation to the log. Again, this could get you both fired and sued if this ever made it to production, but for educational purposes, here’s how to do it
# The Secrect Actions GitHub example has three steps steps: # Show how to print unmasked GitHub secrets to the console - name: Step 1 - Echo out a GitHub Actions Secret to the logs run: | echo "The GitHub Action Secret will be masked: " echo ${{ secrets.SECRET_TOKEN }} echo "Trick to echo GitHub Actions Secret: " echo ${{secrets.SECRET_TOKEN}} | sed 's/./& /g'
GitHub Actions Secret Review
In summary, here are the steps to take if you would like to use a GitHub Actions secret in your continuous integration workflows:
- Go to the Settings tab of your GitHub repository
- Scroll to the GitHub Secrets section of the repo
- Add a new secret, providing an identifier and value for the GitHub secret token
- Reference the GitHub secret in code by prepending the text secret. to the identifier
Follow these steps on how to use a secret GitHub Actions token in GitHub Desktop, and you’ll be able to seamlessly integrate with other systems, without any fear of exposing your passwords to the external world.
 Cameron McKenzie is an AWS Certified AI Practitioner, Machine Learning Engineer, Solutions Architect and author of many popular books in the software development and Cloud Computing space. His growing YouTube channel training devs in Java, Spring, AI and ML has well over 30,000 subscribers.
Cameron McKenzie is an AWS Certified AI Practitioner, Machine Learning Engineer, Solutions Architect and author of many popular books in the software development and Cloud Computing space. His growing YouTube channel training devs in Java, Spring, AI and ML has well over 30,000 subscribers.



