How chmod numbers work explained by example
If you work in a Unix based environment, you need a firm understanding of how chmod numbers work.
For example, you need to know that 777 is a very dangerous permission to provide; 664 is a good mode change for the html directory on an Apache web server; and a chmode number of 898 makes no sense whatsoever.
How chmod numbers work
Admins can assign any combination of three permissions to all files and folders in a Unix based system: read (r), write (w) and execute (x). If you query your rights to a file on Unix, you might see one of these as a result:
- rwx
- r-x
- rw-
- r–
Clever that they are, Unix administrators figured that if each of those three permissions were assigned a numeric value, the various combinations of read, write and execute permissions could be expressed as a single digit. Simply assign execute the value 1, write the value 2, and read the value 4. Then add the user’s rights together and you’ll end up with a unique digit between zero and 7.
Examples of chmod numbers
Here are a few examples of how chmod (change mode) numbers work when permission values are added together:
- A user with read only permissions would have a permission value of 4.
- A user with read and write permissions would have a permission value of 6 (4+2).
- A user with all three permissions would be assigned the value of 7.
Listing of chmod numbers
Here’s a complete table of chmod numbers, along with how to calculate the sum.
| Complete table of chmod numbers | ||
|---|---|---|
| Number | Permission | Sum |
| 0 | – – – | 0+0+0 |
| 1 | – – x | 0+0+1 |
| 2 | – w – | 0+2+0 |
| 3 | – w x | 0+2+1 |
| 4 | r – – | 4+0+0 |
| 5 | r – x | 4+0+1 |
| 6 | r w – | 4+2+0 |
| 7 | r w x | 4+2+1 |
The need to map a file or folder permission may seem overcomplicated at first, but it becomes natural and conversational once you get used to it.
chmod number triplets
In practice, you usually see chmod numbers expressed in triplets such as 762 or 777. That’s because every file and folder in Linux has three different permissions associated:
- One permission for the owner, the person who created the file or folder.
- One permission for all of the people in the same primary group of the owner.
- One permission for everyone else, which includes unauthenticated and anonymous users.
So, if you see a 762 permission assigned to a folder, that means the user who created the folder has full control, members of that user’s group have read and write permissions, and everyone else has read access. This is a permission often assigned to the uploads folder of a web server such as Nginx.
Here’s another way to think about chmod permissions. With a 762 chmod number:
- Anonymous users can access files served to them by the web server — if they do not have read access, web pages won’t load. However, anonymous users aren’t allowed to upload files.
- Users who are part of the folder owner’s group have write permissions. They are allowed to FTP files to the server, and view the changes they make to the website.
- The user who created the folder has full control to read files, delete files, upload new files and even execute scripts.
A chmod number to avoid
In some circles, three sevens are a lucky combination. But Unix admins avoid the 777 chmod permission number, as it gives even anonymous users the right to execute programs in any folder they can see. This opens up your server to malware, ransomware and other nefarious attack vectors. It’s also a risk for users to unknowingly edit or execute files that they shouldn’t be allowed to touch.
Software integration problems are often difficult to troubleshoot, especially if there is confusion about the rights assigned to users and groups who attempt to access a given resource. To discount this permissions problem, new admins may be tempted to recursively assign the 777 chmod number to a directory and all of its contents.
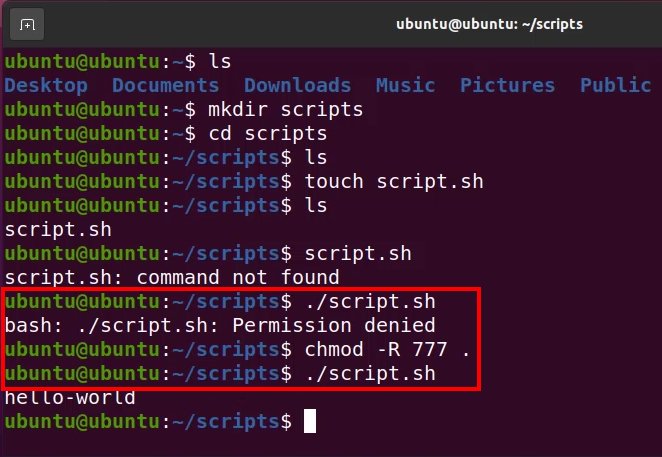
Use of the 777 chmod number typically violates the principle of least privilege. 777 should normally be avoided.
Best practices for chmod numbers
Unfortunately, if the 777 chmod number change doesn’t work, an admin may attempt other troubleshooting tasks and forget to revert the folder to its original permissions. Failure to do that not only puts the system at risk, but it could also cause the system to fail a security or compliance audit. As a rule, sys admins should never to assign 777 rights to a folder. Always observe the principle of least privilege, even when troubleshooting problems.
The Unix command line can be intimidating at first, and initially chmod numbers seem unnecessarily confusing. But once you understand how chmod numbers work, it will all start to make sense and greatly increase your comfort level with assigning permissions using chmod triplets.
 Cameron McKenzie is an AWS Certified AI Practitioner, Machine Learning Engineer, Solutions Architect and author of many popular books in the software development and Cloud Computing space. His growing YouTube channel training devs in Java, Spring, AI and ML has well over 30,000 subscribers.
Cameron McKenzie is an AWS Certified AI Practitioner, Machine Learning Engineer, Solutions Architect and author of many popular books in the software development and Cloud Computing space. His growing YouTube channel training devs in Java, Spring, AI and ML has well over 30,000 subscribers.



